Practical Malware Analysis - Chapter 3 Lab Write-up
Chapter 3. Basic Dynamic Analysis
This details analysis undertaken and answers to the lab questions in Chapter 3.
Lab 3-1
This lab uses the file Lab03-01.exe. Analyse this using basic dynamic analysis tools.
Question 1
What are this malware’s imports and strings?
Answer 1
Looking at a new tool, we’re able to open this up in PE Studio to gain a lot of insight into the file, and determine both its imports and strings.
Based on the low number of imports we can assume this file is packed.
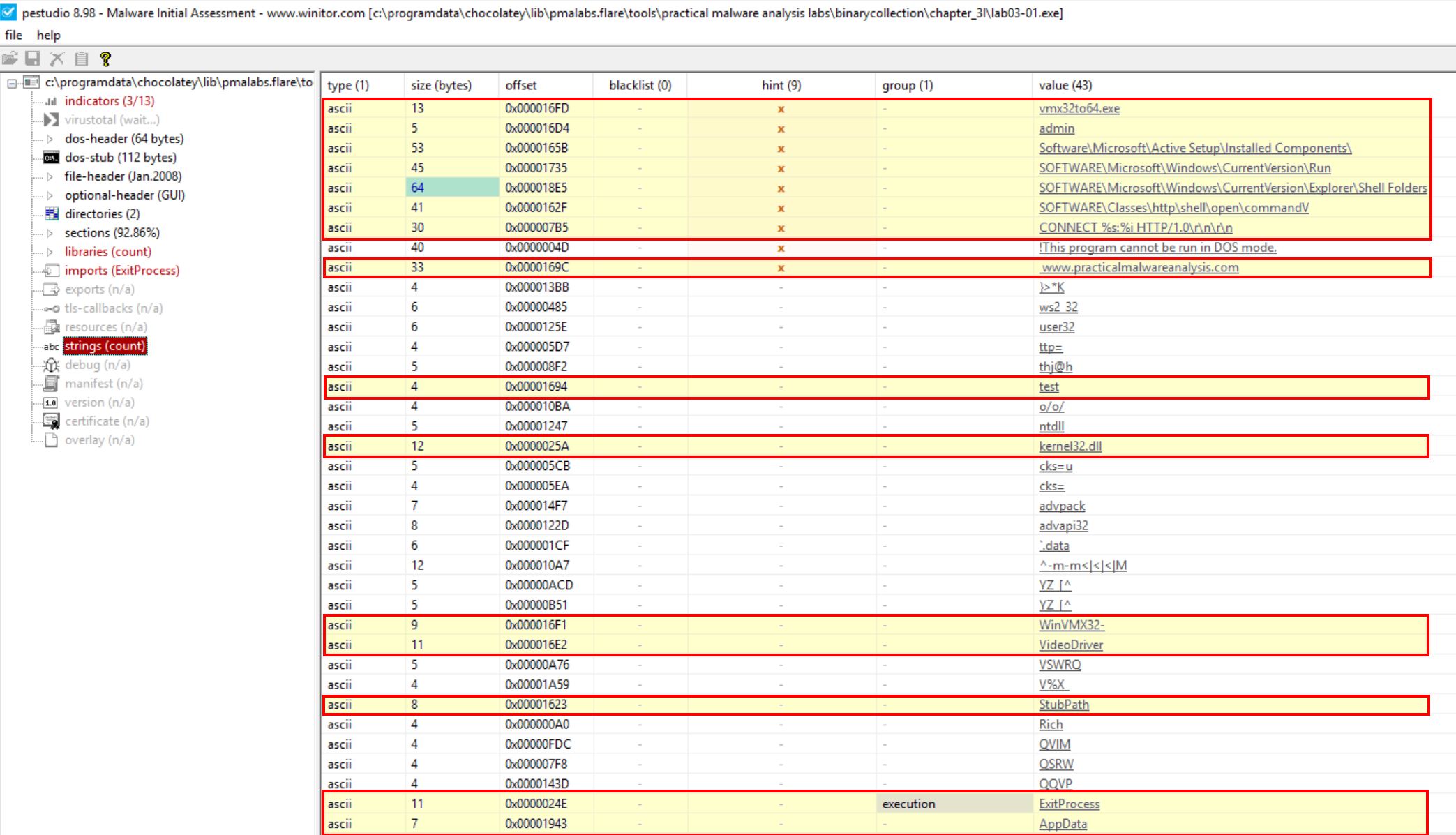
If we take a look at the strings though we see a number of interesting entries which we typically wouldn’t expect to see on a packed file.
Question 2
What are the malware’s host-based indicators?
Answer 2
Attempting to run this file within a Windows 7 and Windows 10 VM causes it to crash and fail.
In todays day and age this piece of malware is detected by almost every AV available but also fails to run properly. This is because like a lot of malware it was created with a certain OS in mind (in this case Windows XP).
By running the malware in a Windows XP environment we are able to see what the original functionality of this file was:
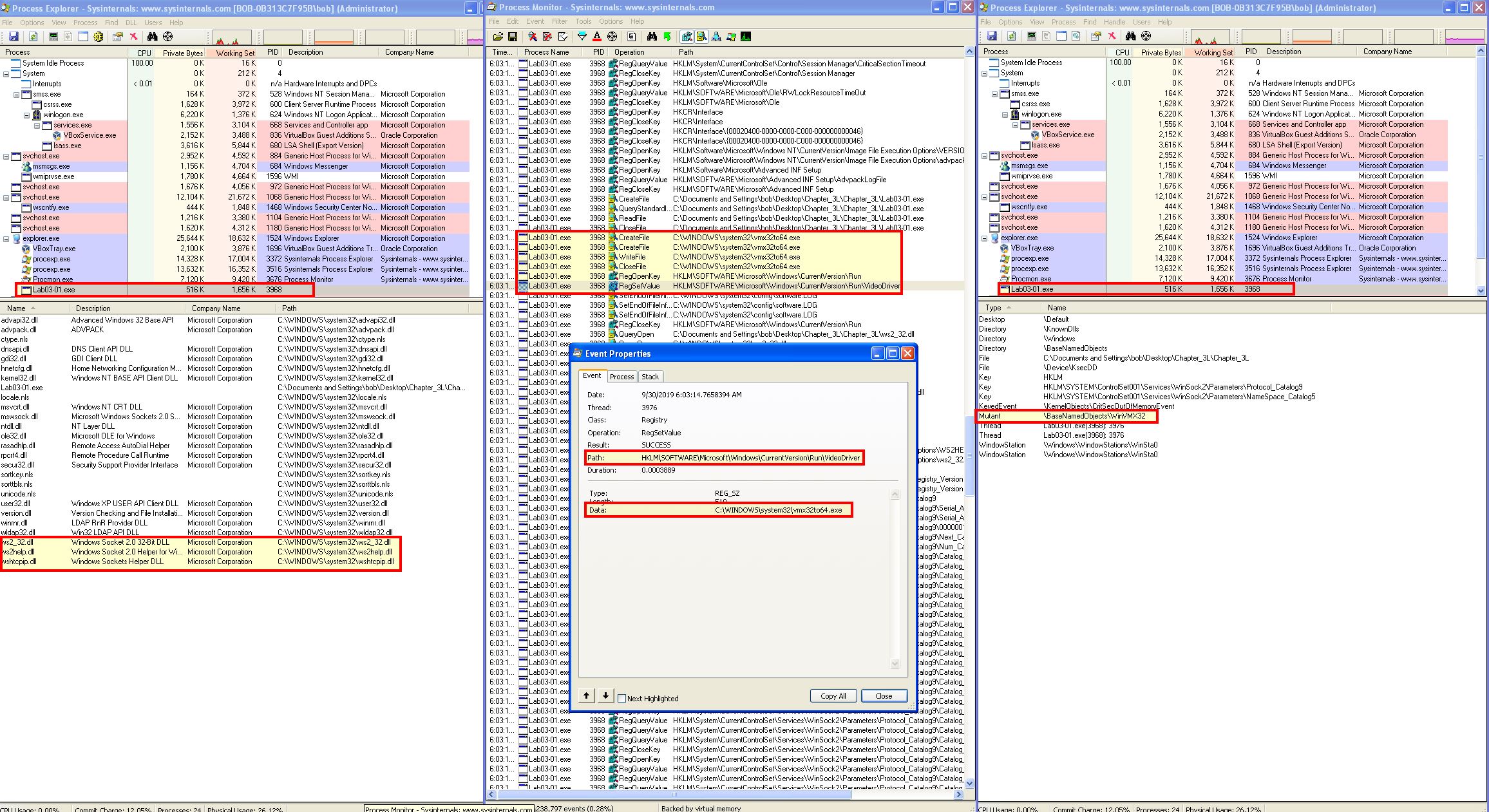
The host based indicators are as follows:
- A Mutex - AKA Mutual Exclusion (this is essentially a lock on a resource), is created for “WinVMX32”.
- The malware is copied to a file called “vmx32to64.exe” which is dropped within C:\Windows\System32.
- A registry key is created at HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\VideoDriver for persistence indicating whenever the system starts it should run the copied malware.
Question 3
Are there any useful network-based signatures for this malware? If so, what are they?
Answer 3
By directing our Windows XP traffic through another host we can use a utility such as Fakenet-NG or ApateDNS to intercept the requests.
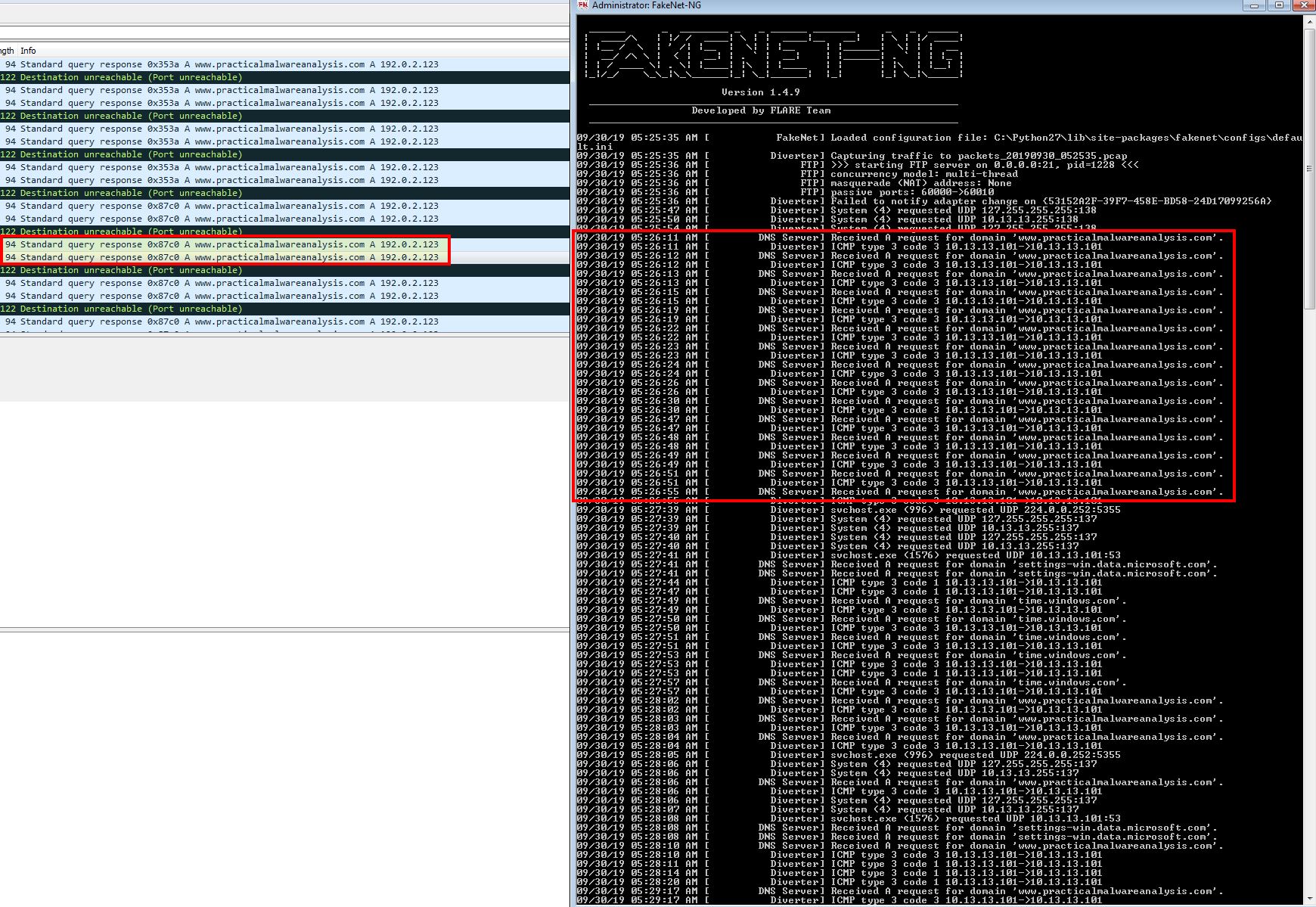
Through doing this we can see the below:
- www[.]practicalmalwareanalysis[.]com is resolved
Had we allowed the malware to establish a connection we would see it sending random beacons of 256 bytes out of random data over port 443.
Lab 3-2
This lab uses the file Lab03-02.dll. Analyse this using basic dynamic analysis tools.
Question 1
How can you get this malware to install itself?
Answer 1
Using PE-bear we are able to easily see the exports of this DLL file. When comparing this with the imports shown in PEview it becomes quite clear that this DLL needs to be installed as a service.
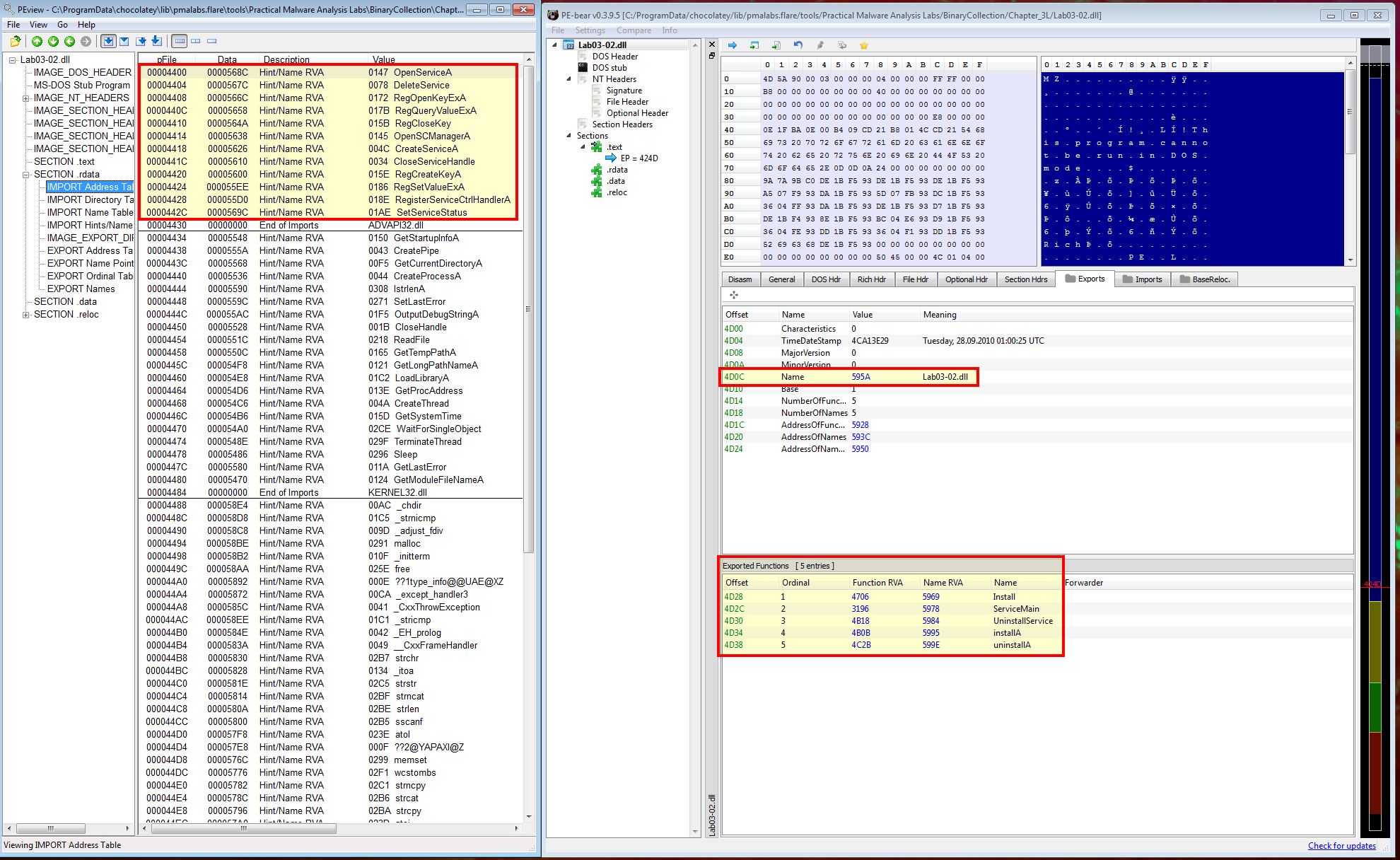
To further validate our assumptions we can run strings over the DLL. Some key elements of interest are shown below:
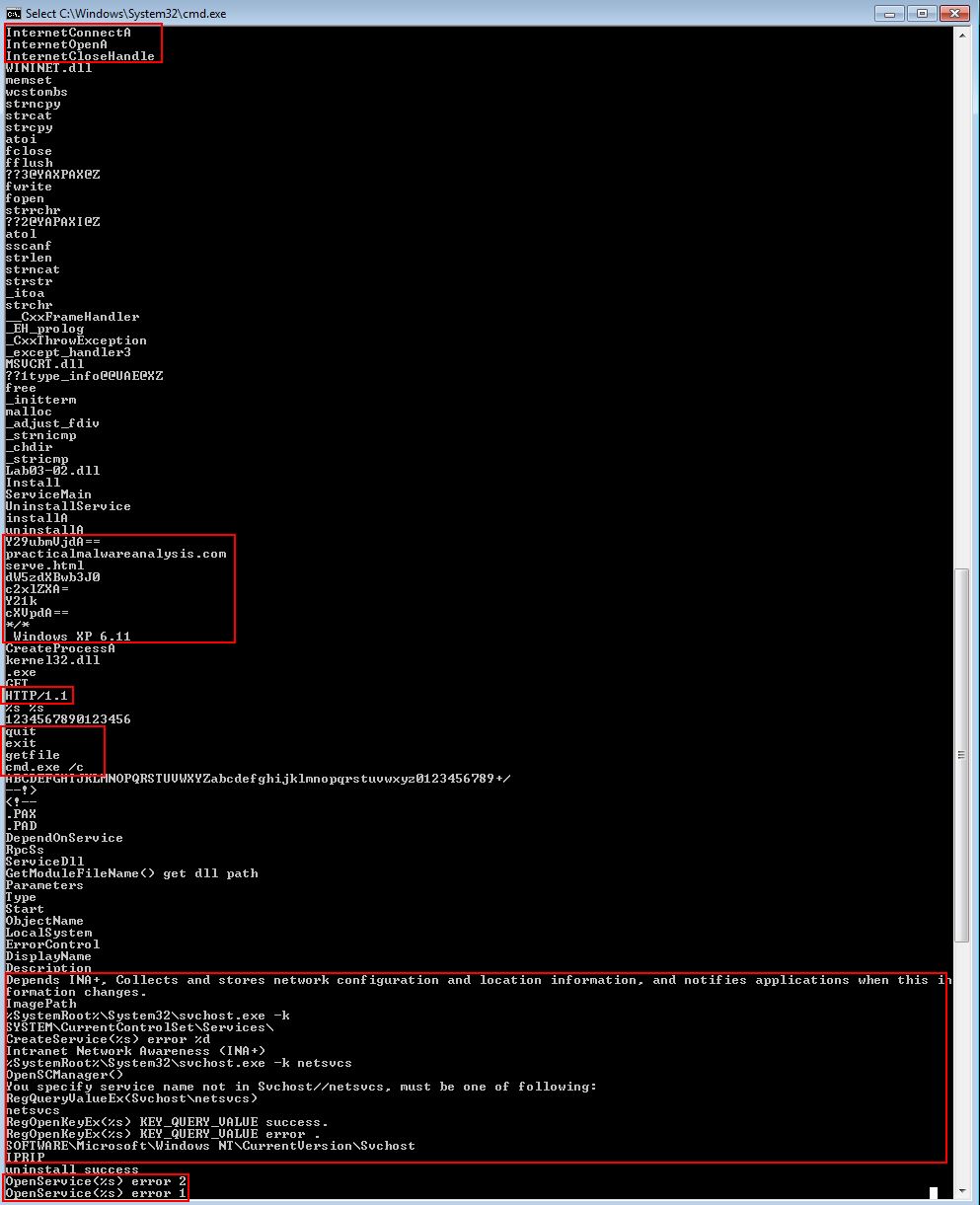
Something to note is the reference to Windows XP 6.11, which means it’s once again likely this was created for, and will only work on, Windows XP.
Back in our Windows XP VM, we’re able to use rundll32.exe and the install exported function to execute this DLL and install it as a service.
rundll32.exe Lab03-02.dll,install
By using regshot we’re easily able to see the registry keys which have been modified by running the DLL.
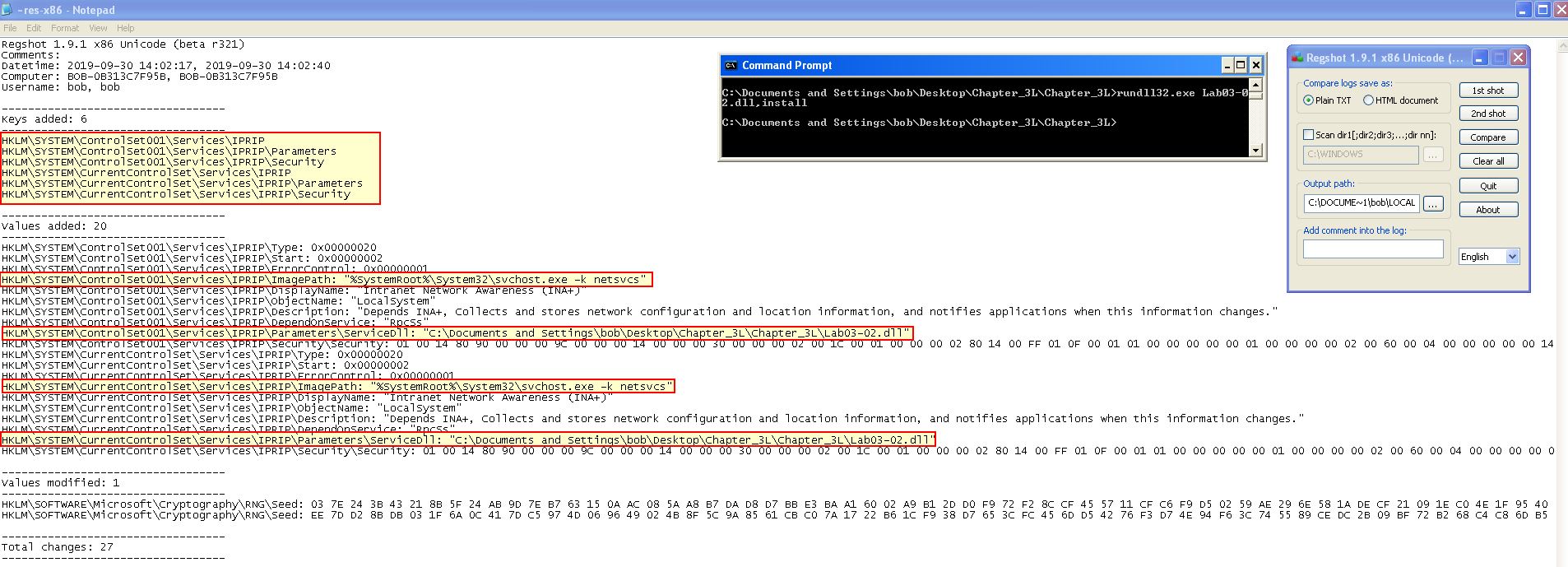
Question 2
How would you get this malware to run after installation?
Answer 2
Given this has installed as a service and we know the name is IPRIP we can run it through either the net utility, or SC Tool.
sc start IPRIP
net start IPRIP
Question 3
How can you find the process under which this malware is running?
Answer 3
By searching for the specified DLL, or looking at the DLLs loaded by a process in Process Explorer, we’re able to get the process ID of the svchost process which is running this malware.
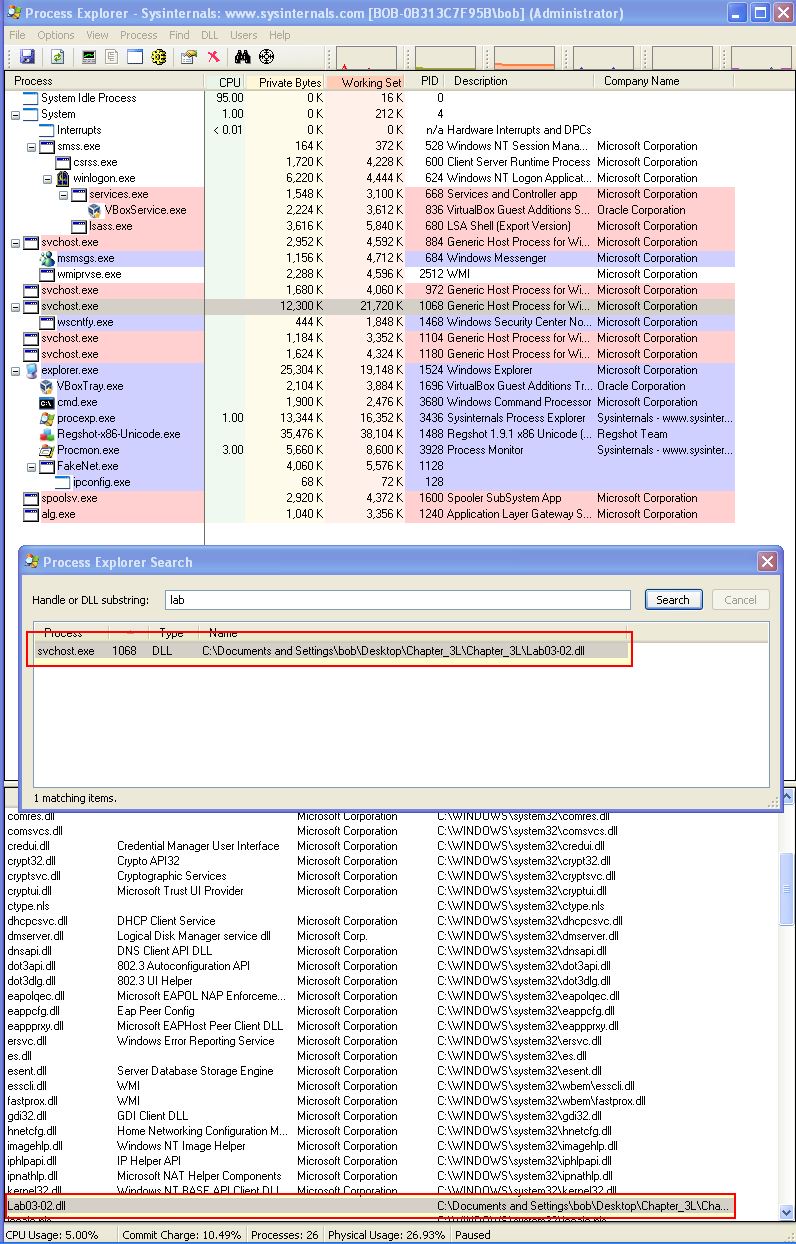
- 1068
Question 4
Which filters could you set in order to use procmon to glean information?
Answer 4
Because there’s likely to be multiple svchost processes, we can filter by the Process ID to glean information only on the svchost process responsible for running this malware.
Question 5
What are the malware’s host-based indicators?
Answer 5
By examining the service which is created we can get a number of host-based indicators.
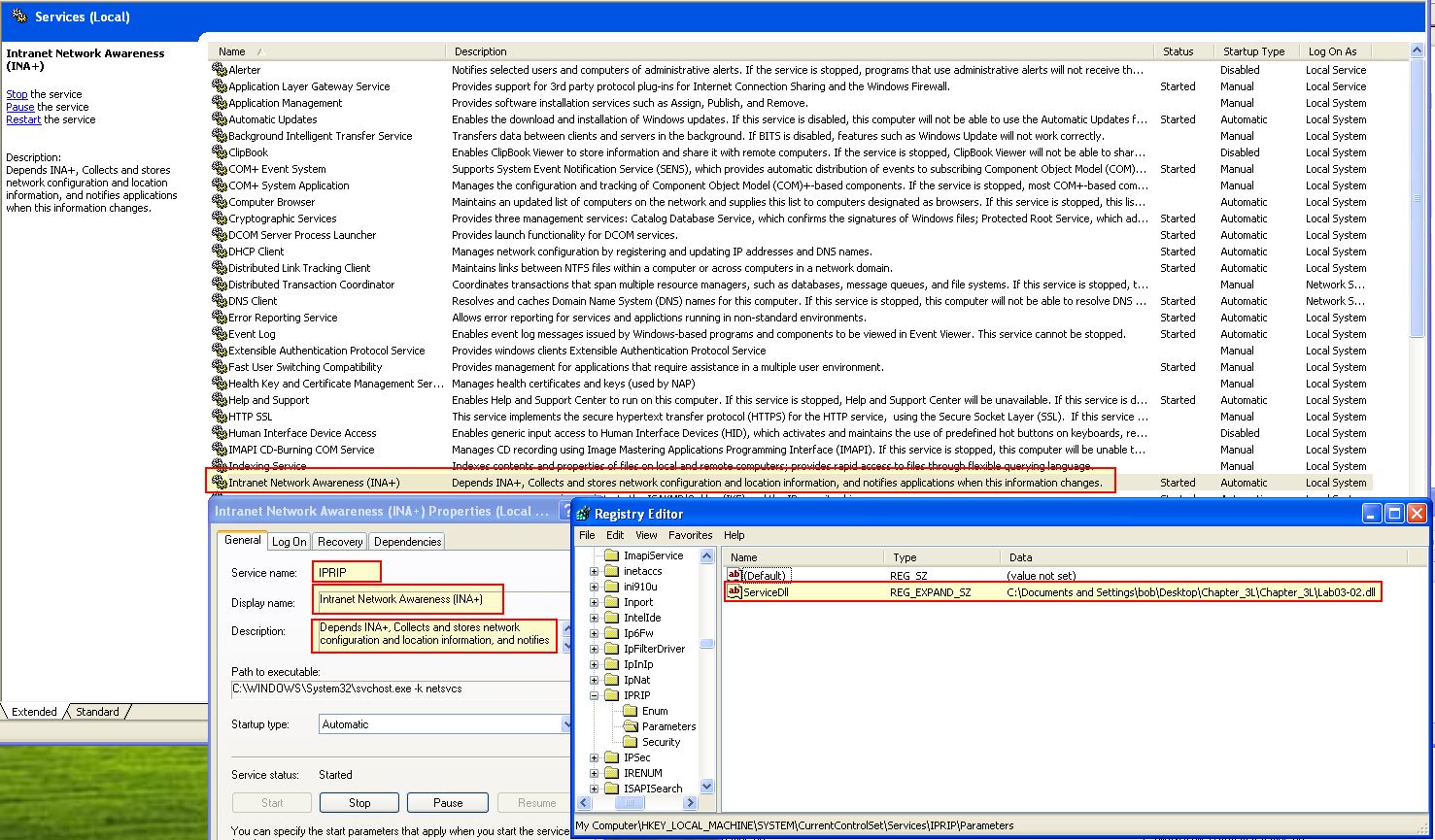
- IPRIP
- Intranet Network Awareness (INA+)
- Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes.
- HKLM\SYSTEM\CurrentControlSet\Services\IPRIP\Parameters\ /v servicedll
Question 6
Are there any useful network-based signatures for this malware?
Answer 6
By running Fakenet on the host we’re able to intercept the malware’s request and determine what it is sending to a remote server. In this case it uses a specified domain name, uses port 80, always fetches a specific file, and uses a custom but unique User-Agent.
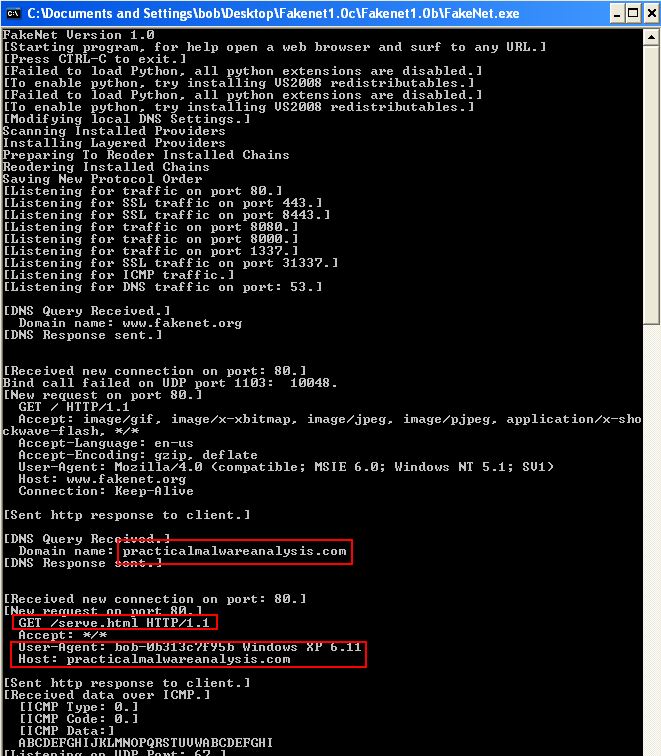
- practicalmalwareanalysis[.]com
- port 80
- serve.html
- User-Agent %ComputerName% Windows XP 6.11
It’s at this point that the string previously discovered as ‘Windows XP’ has context.
Lab 3-3
This lab uses the file Lab03-03.exe. Analyse this using basic dynamic analysis tools.
Question 1
What do you notice when monitoring this malware with Process Explorer?
Answer 1
If we monitor this malware with Process Explorer we can see it briefly spawns svchost before both processes vanish.
At this point if we look closer into the memory strings of running svchost processes, we can see that this malware has used process replacement (more commonly known as process hollowing nowadays) to execute under the guise of a svchost process.
Question 2
Can you identify any live memory modifications?
Answer 2
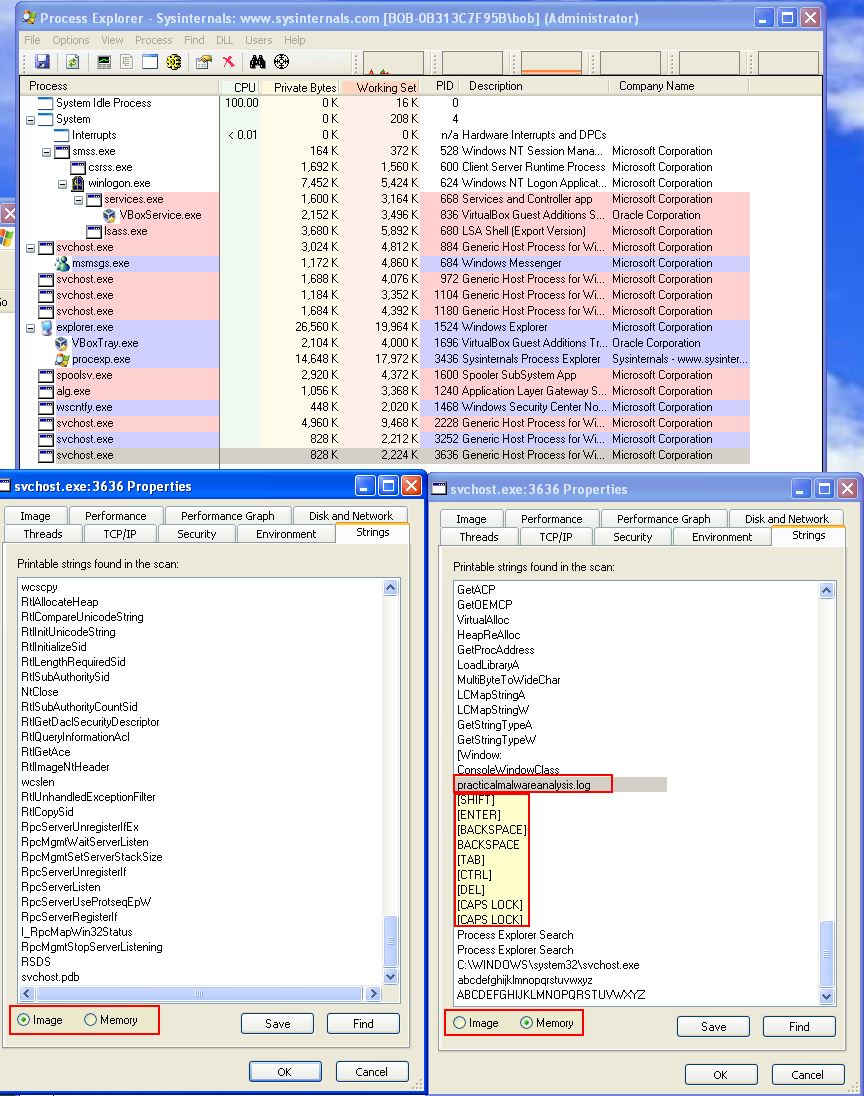
As mentioned by looking into the live memory of svchost we can see the strings differ significantly on disk to what is in memory.
Question 3
What are the malware’s host-based indicators?
Answer 3
We can see both in memory, and on disk that the malware creates a file called practicalmalwareanalysis.log
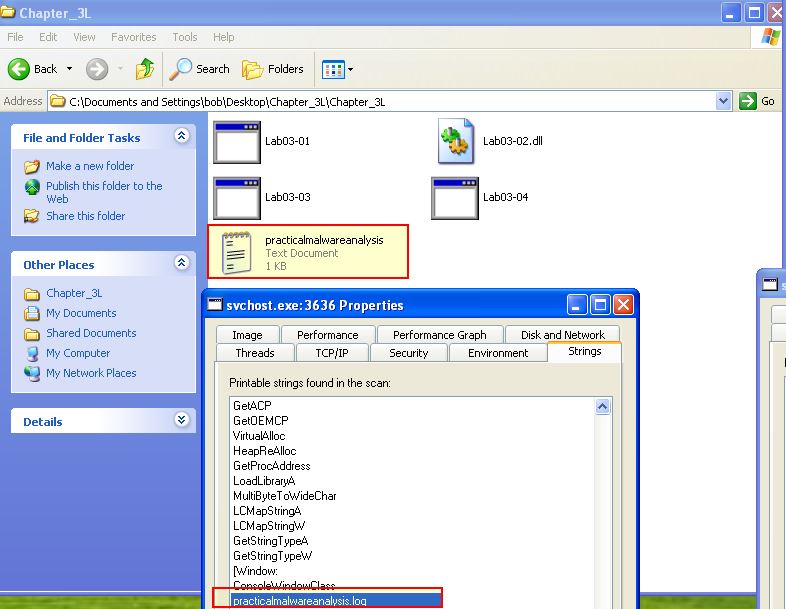
- practicalmalwareanalysis.log
Question 4
What is the purpose of this program?
Answer 4
By opening wordpad and typing out some content, we can then open up practicalmalwareanalysis.log and see that it has logged all of our keystrokes.
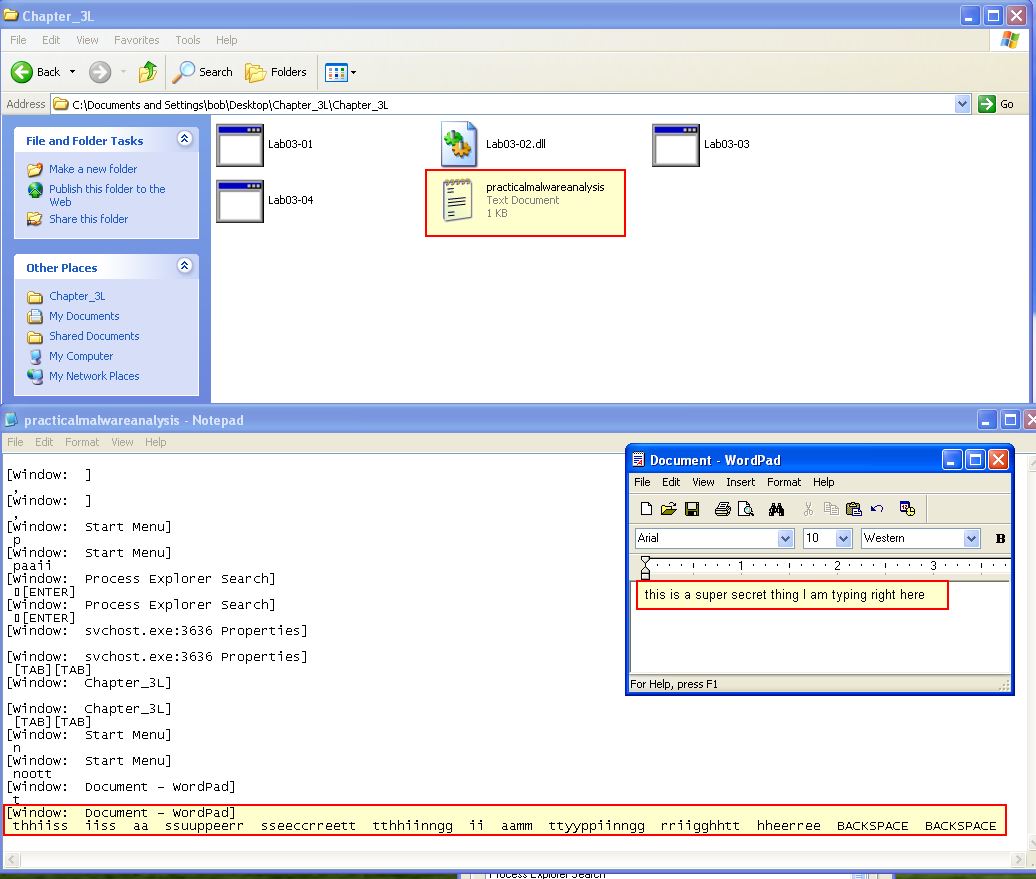
From this we can conclude that this uses process hollowing to run a keylogger on the infected machine through svchost.exe
Lab 3-4
This lab uses the file Lab03-04.exe. Analyse this using basic dynamic analysis tools.
Question 1
What happens when you run this file?
Answer 1
When we run this file it immediately deletes itself. We can see this event coming from the program spawning a del (delete) command from a command prompt.
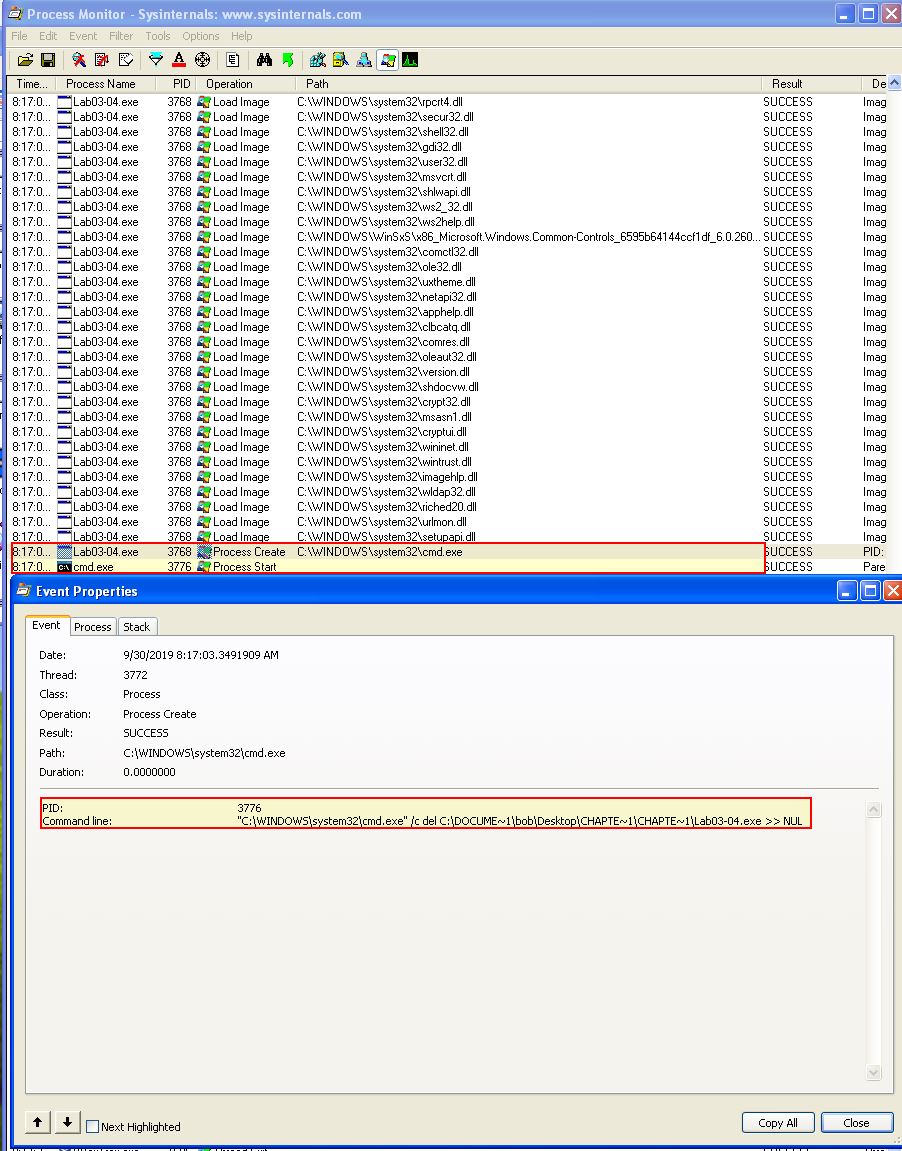
Question 2
What is causing the roadblock in dynamic analysis?
Answer 2
This could be caused by command line parameters needing to be passed to the program, it needing to fetch a particular file from a remote location, it detecting it is in a sandbox, it only targeting a particular timezone, or it only running on a specific domain. Some clues can be found by looking at the program strings.
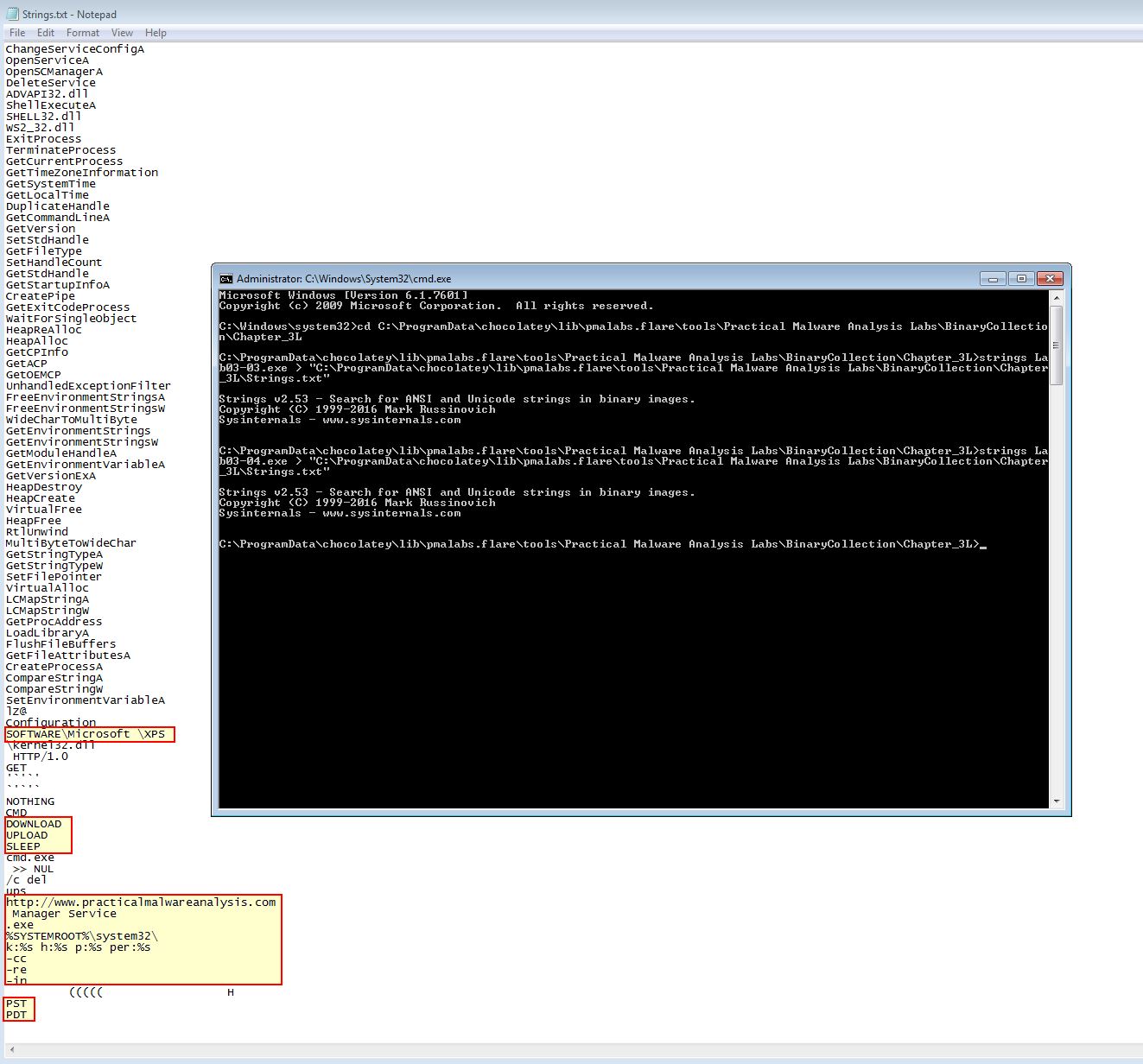
Question 3
Are there other ways to run this program?
Answer 3
Attempting to run with the below enumerated through strings still results in the file being deleted, so at this stage we cannot do much more; however, this will be revisited in lab 9.
- cc
- re
- in
This concludes chapter 3, proceed to the next chapter.